Men In Black: Difference between revisions
m Added FISA 702 |
m Added DI&W section |
||
| (4 intermediate revisions by the same user not shown) | |||
| Line 18: | Line 18: | ||
=== Secret Surveillance Warrants (FISA 702) === | === Secret Surveillance Warrants (FISA 702) === | ||
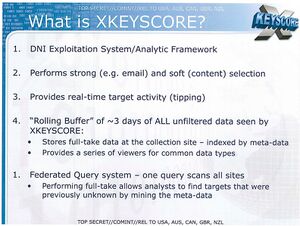
[[File:NSA-X-Keyscore-slide-001.jpg|thumb|X-Keyscore is one of the tools used to prosecute FISA 702 warrants against surveillance targets. According to whistleblowers, even mentioning the codeword IMMACULATE CONSTELLATION would trigger automatic surveillance under a warrant issued by a secret FISA court.]] | |||
According to Michael Shellenberger, some programs are so sensitive that mentioning them in public can trigger automatic FISA 702 surveillance warrants. | According to Michael Shellenberger, some programs are so sensitive that mentioning them in public can trigger automatic FISA 702 surveillance warrants. | ||
FISA 702 warrants are secretive court orders first exposed by whistleblower Edward Snowden in 2013 when he outted a littany of NSA secret spy programs. | FISA 702 warrants are secretive court orders first exposed by whistleblower Edward Snowden in 2013 when he outted a littany of NSA secret spy programs. | ||
=== Unacknowledged Special Access Carve-outs === | |||
Another method used to hide UAP data from the military/government officials tasking the collection assets is through the use of highly classified programs that create bottlenecks. By creating bottlenecks in the official channels this data transits along its course from asset -> tasking official, the architects of UAP-secrecy can effectively gatekeep. By depriving the military intelligence enterprise of this information, they are denying the entire defense ecosystem the ability to recognize, monitor, counter and catalog UAP. One such example of this type of program is [[Immaculate Constellation]], an Unacknowledged SAP intended to intercept high fidelity intelligence about UAP collected by tasked and untasked US platforms. | |||
=== Deceptive Indications & Warnings === | |||
A subset of highly classified techniques designed to fool a system or individual into obscuring the source of an action or deceiving the intended audience as to the actor's intent. This is commonly referred to as a "false flag" - one such prominent instance being Operation Northwoods. | |||
== Noteable Incidents == | == Noteable Incidents == | ||
1) [[Dreamland Resort Raid]] - Nov, 3 | 1) [[Dreamland Resort Raid]] - Nov, 3 2022 raid on the webmaster of DreamlandResort.com for reasons still unknown.<ref>Area 51 FBI [https://www.area51fbiraid.com/ Raid]</ref> | ||
2) The 1970's-1980's era information war against the UFO community via [[Paul Bennewitz]] and others.<ref>https://archive.org/details/mirage-men-2013</ref> | 2) The 1970's-1980's era information war against the UFO community via [[Paul Bennewitz]] and others.<ref>https://archive.org/details/mirage-men-2013</ref> | ||
| Line 33: | Line 40: | ||
5) [[Immaculate Constellation]] - A program disclosed in 2024 by journalist Michael Shellenberger. According to multiple whistleblowers, simply mentioning these words qualified you for a FISA warrant. FISA 702 warrants are secret court orders for surveillance. | 5) [[Immaculate Constellation]] - A program disclosed in 2024 by journalist Michael Shellenberger. According to multiple whistleblowers, simply mentioning these words qualified you for a FISA warrant. FISA 702 warrants are secret court orders for surveillance. | ||
== | == References == | ||
Latest revision as of 04:51, 16 November 2024
also see: Deceptive I&W, Counter-intelligence, Disinformation, Suppression

The Men In Black are entities commonly witnessed in the orbit of UFO sightings and encounters. UFO-lore holds them to be anything from special interest groups acting outside the law to deep-black federal agents. Some even suggest they are the visitors, themselves. What's clear is that witnessing a UFO or researching the topic could result in a visit from the Men In Black. While their interest in the subject is unknown, they are generally seen as a negative force who will work to cover-up information about UFO/NHI at any cost. For the purposes of this topic, it can be assumed that MIB's may actually represent more than one (or even all) of these possible sources.
Tools of the Trade - Architects of Denial[edit | edit source]
Whoever or whatever the Men In Black are, their goal of suppressing information and denying knowledge of NHI is accomplished using a variety of tools.
When managing government and military insiders, they have powerful tools available that by default do not generate activity in the public space. Unlike an arrest or outright disappearance, the revocation of a security clearance or degredation of status among one's peers is difficult to measure and report on. Given the sensitive nature of some of this work, its also very difficult to pin down and prove to anyone but the person at the receiving end of it.
Disinformation Campaigns/Information Warfare[edit | edit source]
Disinformation is a broad topic among the even broader topic of information warfare. For the purpose of UFO research, disinformation involves the deliberate creation and release of false information (documents, AV, sensor, etc) for the purpose of eliciting some tactical goal. This often includes portions of legitimately sensitive material in order to "hook" the reader in and sell the lie, according to AFOSI Special Agent Richard Doty. Disinformation is a technique that is used to bring about a goal, overall this is known as information warfare, or the weaponization of information to deny, deceive, disrupt, degrade or destroy our understanding/comprehension/discovery/dissemenation of UFO material.
Suppression[edit | edit source]
Suppression in this context refers to preventing an individual from speaking out by threat or actual use of coercive tactics. This could be ridicule, spreading rumors at work, psychological intimidation tactics or worse. Ruining a reputation that took a whole career to build has no price tag, nor is it insurable.
Administrative Terrorism[edit | edit source]
Administrative Terrorism is a term coined by whistleblower David Grusch. He used it to refer to the government's objective of maintaining secrecy at all costs, as a vehicle or means by which they further this objective. Although an overlap exists with this and "suppression" activities, it is generally far more severe. Grusch referred to people involved in driving incidents, being physically harmed or even murdered in some cases.
Secret Surveillance Warrants (FISA 702)[edit | edit source]
According to Michael Shellenberger, some programs are so sensitive that mentioning them in public can trigger automatic FISA 702 surveillance warrants.
FISA 702 warrants are secretive court orders first exposed by whistleblower Edward Snowden in 2013 when he outted a littany of NSA secret spy programs.
Unacknowledged Special Access Carve-outs[edit | edit source]
Another method used to hide UAP data from the military/government officials tasking the collection assets is through the use of highly classified programs that create bottlenecks. By creating bottlenecks in the official channels this data transits along its course from asset -> tasking official, the architects of UAP-secrecy can effectively gatekeep. By depriving the military intelligence enterprise of this information, they are denying the entire defense ecosystem the ability to recognize, monitor, counter and catalog UAP. One such example of this type of program is Immaculate Constellation, an Unacknowledged SAP intended to intercept high fidelity intelligence about UAP collected by tasked and untasked US platforms.
Deceptive Indications & Warnings[edit | edit source]
A subset of highly classified techniques designed to fool a system or individual into obscuring the source of an action or deceiving the intended audience as to the actor's intent. This is commonly referred to as a "false flag" - one such prominent instance being Operation Northwoods.
Noteable Incidents[edit | edit source]
1) Dreamland Resort Raid - Nov, 3 2022 raid on the webmaster of DreamlandResort.com for reasons still unknown.[1]
2) The 1970's-1980's era information war against the UFO community via Paul Bennewitz and others.[2]
3) Harold Dahl's 1947 intimidation and subsequent recantation following the Maury Island Incident.[3]
4) Richard Doty's presense as a N.M. State Trooper during a raid on whistleblower Bob Lazar's home ostensibly for dangerous nuclear materials. Doty has stated his presense was entirely unrelated to his past work in the USAF.
5) Immaculate Constellation - A program disclosed in 2024 by journalist Michael Shellenberger. According to multiple whistleblowers, simply mentioning these words qualified you for a FISA warrant. FISA 702 warrants are secret court orders for surveillance.

